

National Trading Standards (NTS) are warning the public that criminals are using fake online reviews to sell poor quality goods and services.
It has become a common practice for a lot of people to seek reviews prior to making a purchase, but how do we know whether the reviews we read are genuine?
The following guidance is from NTS:
• Timing and spacing – check for multiple similar reviews that have been uploaded within a few minutes or hours.
• Check the reviewer’s activity – if an account has been activated recently or has only reviewed a narrow range of products/services, it could indicate suspicious activity.
• Vague language – legitimate reviews will often be personal and specific to the individual’s experience. A fake is more likely to be vague, using generic words and phrases such as ‘amazing’, ‘awesome’ and ‘buy this product’.
• Check contact details – if a reviewer is happy to be contacted with questions, and is responsive, it’s a good sign they’re legitimate.
• Use a browser plug-in – they use artificial intelligence to analyse reviews, identify suspicious activity and suggest better alternatives. Examples are Fakespot and ReviewMeta.
• Look beyond the star rating – whilst a star rating of 4.5 or 5 can be a good quality indicator, be sure to look at the reviews too.
For further information and advice visit Online shoppers buy 80 million ‘disappointing’ items based on rave reviews – National Trading Standards
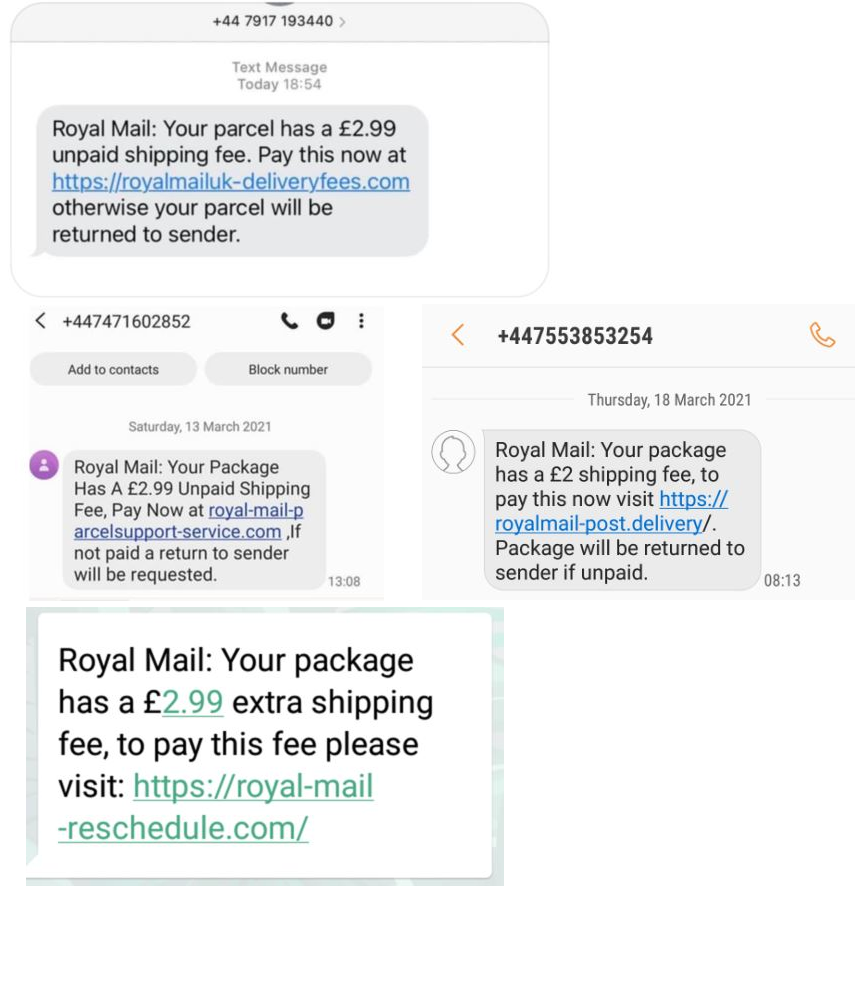
The Cambridgeshire and Peterborough Against Scams Partnership, are warning us all of a scam text message purporting to be from Royal Mail.
On the 13th October 2020, Microsoft released a significant update to all users of Windows 10 OS. (CVE-2020-1047) (If you use Windows OS on a work computer, then updates may be managed by your ICT)
The update fixes 87 vulnerabilities with one having a Microsoft severity score of 9.8 out of 10 and has been described as dangerous. This bug can allow a criminal to take over any Windows operating system that has not been patched.
The second issue of note relates to Outlook in which the bug can be exploited by tricking the user into opening a specially crafted file with an affected version of the Microsoft Outlook software.
You may already have updates set to Automatic, but please check just in case the updates have not been applied.
To do this, click on the magnifying glass on the taskbar bottom left of your screen, then in the search bar start typing ‘windows update’, and you will then see Windows Update Settings appear, click on this and follow the instructions.
Attached here is an important scam alert from the City of London Police, National Fraud Intelligence Bureau.
Should the content of the document raise any questions or issues, then please contact Mr Nigel Sutton 8517, Cyber Protect Officer.
Please consider forwarding to family and friends and any appropriate community group.
You wouldn’t let a thief enter your home, but what if the thief was masquerading as someone familiar, such as a postman, and tricked you into opening the door? Phishing works in a similar way – criminals use legitimate-looking messages and websites to trick people into opening the doors to their personal data, giving up logins, passwords or even payment details. That information can then be used to commit fraud and cyber crime.
Phishing attacks are a common security challenge that both individuals and businesses across the UK face on a regular basis.
The National Cyber Security Centre’s Suspicious Email Reporting Service (SERS) received over 1.7M reports from the public between April and August 2020, with the most commonly faked brands being TV Licensing, HMRC and GOV.UK.
Many of the phishing scams that get reported to us have one thing in common, they started with a message out of the blue. Whether it’s an email asking you to “verify” account information, or a text message claiming to be from your bank, the goal of a phishing attack is usually the same – to trick you into revealing personal and financial information.
Criminals are experts at impersonation and they’re constantly getting better at creating fake emails and texts that look like the real thing. Here’s some simple advice you can follow when it comes to dealing with phishing scams:
1 – Remember, your bank, or any other official organisation, won’t ask you to share personal information over email or text. If you need to check that it’s a genuine message, call them directly. Don’t use the numbers/emails in the email, but visit the official website instead.
2 – If you have received an email which you’re not quite sure about, forward it to the Suspicious Email Reporting Service (SERS):
report@phishing.gov.uk. If it turns out to be a malicious, your report will help other people from falling victim to it.
3 – Received a text message you’re not quite sure about? Maybe it’s asking you to “verify” personal or financial details, such as a banking password? You can report suspicious text messages by forwarding them to 7726.
4 – If you’ve lost money or provided personal information as a result of a phishing email, notify your bank immediately and report it to
Action Fraud: www.actionfraud.police.uk
For more simple tips on how to protect yourself online, visit: www.actionfraud.police.uk/cybercrime
You may already have seen or used the QR (Quick Response) code like the one above, but since pandemic measures have been relaxed, the QR code is being seen more often especially in pubs and restaurants.
So what is the QR code? It is simply a shortcut to a webpage, just like the link or shortcut we are used to in an email or other electronic messages.
To read the QR code, simply point your phone camera at it and your smart phone will read it and tell your phone browser to display the webpage it relates to, it is that simple. (There are also QR code reading apps available)
People like shortcuts, and criminals know we do.
Although the use of the QR code has benefits just like the link or shortcut in an email, it could be exploited by cyber criminals so I just want you to know how, and then you can make your own mind up whether to scan or not.
The image below was taken in a shopping centre the QR code is printed on a professional looking 5 foot high banner outside the shop. Because the banner looks high quality and is in a secure shopping centre with cameras and security, it unlikely that it had been placed there by a criminal. (Not guaranteed of course, but on balance I would scan it but not provide any personal information)
Another example of when I would consider scanning a QR code, would be when I have entered a restaurant or pub, and on the table is a guide to ordering food and drinks. The laminated sheet gives me the choice of downloading an app from Google Play or the App Store, or I can scan the QR code.
If however, I was in public and I read a poster with a QR code on it advertising a service or product, I will be far more cautious of scanning it because it is in a far less secure environment which a criminal could exploit. How? It is technically possible for the criminal to create their own QR code, print it and place it over the original QR code on the poster, they then create a fake website and have it hosted on the internet. If this QR code is scanned by a third party then their device will display a fake website deceiving the user to submit private information to the criminal. Exactly how phishing emails work.
So, if you are going to scan a QR code, just assure yourself that the QR code you are scanning is genuine, does the poster look genuine? Is it printed to a high commercial standard? Can you tell if there is another layer of paper over the QR code that suggests the poster has been tampered with? If in doubt, don’t scan it, and if you want to find out more about what the poster is advertising, consider using your browser on your device.
The good news, I am yet to read a crime report that suggests anyone in the UK has been caught out in such a way, could this change in the future?
Being aware of the tactics used by cyber criminals to steal our data and money, helps us to defend ourselves and families.
If you have any questions or concerns involving QR codes, then please contact:
Mr Nigel Sutton 8517
Cyber Protect Officer
Serious & Organised Crime (Intelligence and Specialist Crime Department)
Ext: 01480 422773

For organisations whose hardware, software and data where the centre is located on site and directly under their control, organisations are free to determine their own security posture and policies. However, much of this oversight is lost when migrating to the Cloud. Most Cloud providers share a pool of resources between hundreds, if not thousands of other users.
Organisations may use the hardware and software provided – Software as a Service (SaaS). Other organisations want hardware and IT infrastructure – Infrastructure as a Service (IaaS). Some want something in between – Platform as a Service (PaaS). Each model places different levels of responsibility on the customer. Organisations must be clear what security measures they are expected to take and where the responsibilities lie.
The following points to take note when checking your security responsibilities:
1. Does the cloud encrypt stored data? Who has control of the encryption keys, if it’s the cloud provider how do you know that they will be kept secure?
2. When your data travels over the internet, will it be encrypted? A VPN gives a high degree of privacy when communicating with cloud applications.
3. When changing providers, or leaving the cloud environment, organisations need to know that data will be removed from all hard drives. In the cloud these resources will be reallocated to other users. Check how the provider intends to make data inaccessible to others and what guarantee they offer.
4. Many cloud providers offer self-service portals where you can access reports, logs. Check with the provider what these show and whether they give you adequate visibility of security incidents.
5. Check that any software used has been developed with security in mind.
6. Using the cloud is often seen as a way to provide business continuity and recovery. What if your cloud provider has problems? Check what redundancy and resilience the Cloud Provider has.
What is sensitive, private and confidential? Employees need to understand how valuable or sensitive data is, then it is more likely to be handled with the care and attention it deserves.
Most security incidents occur because of poor security policies. If employees are using poor passwords to connect to systems, or have access beyond that actually needed to do their job, then invest time and effort educating users.
Check that employee are trained to use applications correctly.
We are seeing a growing trend of so called ‘sextortion’ phishing emails. This is where the sender claims to have compromising images of the recipient and often the email will include a password that the victim has previously used, to add authenticity. Advice from Action Fraud.
These are fundamentally different to actual sextortion attempts where the sender does possess compromising images of the victim. The advice for this remains the same; anyone who is sent an email which includes compromising images and/or a request for payment should contact their local police force.
The free vouchers scam has moved to a new variant with phishing emails being sent to recipients claiming to be from Tesco, offering free vouchers. The email features a link for recipients to register and claim their free voucher which provides an opportunity for criminals to steal email logins, passwords and personal details.
A recent fraud involved the sale of a car where the suspect used the Covid19 lock down as a reason the victim could not see the vehicle and persuaded the victim to pay by bank transfer.
Reporting to Action Fraud can be done online or by calling 0300 123 2040. To report offers of financial assistance from HMRC, contact phishing@hmrc.gov.uk.
This advice has been collated by the East Midlands Regional Organised Crime Unit (ROCU) and is intended for wider distribution to raise awareness among businesses and the public.Advice and information is changing daily as we navigate our way through the COVID-19 pandemic, so please ensure you only take information from reputable sources.
If you require any further information, assistance or guidance please contact the ERSOU Protect Team CyberProtect@ERSOU.pnn.police.uk or your local Force protect team.
Message from: Mr Nigel Sutton 8517, Cyber Protect Officer.
Working together to deliver an inclusive and professional policing service with: Fairness, Integrity, Diligence and Impartiality
This is an important information on the use of Two-factor (2FA) or Multi-factor (MFA) authentication on business and private online accounts.
Using 2FA and MFA means that even if criminals compromise an account password, they will be prevented or disrupted from gaining access, because they will not know the code generated by your account and sent to your mobile phone, or whatever option you have used in the MFA setup.
A quick example of its importance. The person has a Gmail account with 2FA set up on it, a couple of days ago the person received a text message from Google that stated an attempt had been made to access their account from Taiwan. If that person had not have 2FA setup, the cyber criminal would have been in the account quietly stealing private data, and possibly sending out phishing emails to all his contacts which would have appeared to have come from him.
For businesses and individuals using Office 365, please bear in mind the following fact:
Microsoft has reported that 1.2 million Office 365 accounts are compromised every month, which could be cut by 99.9 per cent if organisations enforced multi-factor authentication.
For advice about setting up 2FA and MFA, please visit:
https://www.ncsc.gov.uk/guidance/setting-two-factor-authentication-2fa
The National Cyber Security Centre. (NCSC) Helping to make the UK the safest place to live and work online. www.ncsc.gov.uk
Message from Mr Nigel Sutton 8517, Cyber Protect Officer
Action Fraud are aware of a rumour currently circulating via WhatsApp, SMS and social media which references the City of London Police Fraud Team and claims that Danske Bank customers are being targeted by a particular text message (smishing) scam. The content of this message is false.
However, smishing scams are common. Don’t click on the links or attachments in any suspicious emails or texts, and never respond to messages that ask for your personal or financial details. It’s important to remember that your bank would never ask you to move money out of your account, or contact you out of the blue and ask for details such as your full banking password or PIN number.
Anyone who has divulged information after receiving this type of message should contact their bank immediately.Fraudulent websites are also being set-up, which offers an antivirus program to protect users against the coronavirus. Fraudsters trick users into downloading a remote access Trojan and install malware that could infect the user’s device. Once access has been obtained, the fraudster could act as a legitimate user but use this access to steal data and seek financial gain.
To report fraud or cyber crime, and for advice on how to avoid it visit www.actionfraud.police.uk

Businesses are contacted by someone pretending to be one of their suppliers and told they have changed their bank, requesting they amend the direct debit to reflect this. The genuine supplier then gets in touch to ask what happened to the monthly payments.
Verify all invoices, as well as requests to change bank account details. To check a request is legitimate, contact the supplier directly using established contact details you have on file.
To report fraud or cyber crime, and for advice on how to avoid it visit www.actionfraud.police.uk